Cyberattacks are growing in complexity, with 60% of security breaches linked to poor configurations, according to IBM’s cost of a data breach report 2024. A single misconfiguration can expose sensitive data, making compliance with industry best practices more critical than ever. That’s where CIS compliance plays a vital role.
What is CIS compliance?
CIS compliance refers to adhering to the security benchmarks and best practices established by the Center for Internet Security (CIS). These benchmarks provide globally recognized guidelines for securing operating systems, cloud environments, network devices, and enterprise applications. Organizations that align with CIS compliance strengthen their security posture and reduce the risk of cyberattacks.
CIS benchmarks: setting the gold standard for security
Building a strong cybersecurity foundation starts with a structured approach, and that’s exactly what the CIS compliance framework provides. It helps organizations implement, manage, and maintain security best practices through two key components:
CIS controls – A prioritized set of security actions designed to protect against evolving cyber threats.
CIS benchmarks – Configuration guidelines that secure systems, including Windows, Linux, cloud services, and network devices.
CIS benchmarks go beyond general guidelines by providing specific, actionable steps to lock down critical systems, such as:
- Restricting access to prevent unauthorized logins.
- Automating patching to eliminate known vulnerabilities.
- Continuously monitoring for security deviations before they become threats.
With a well-defined security strategy rooted in CIS benchmarks, businesses can significantly lower the risk of breaches while ensuring compliance with industry standards.
How to achieve CIS compliance ?
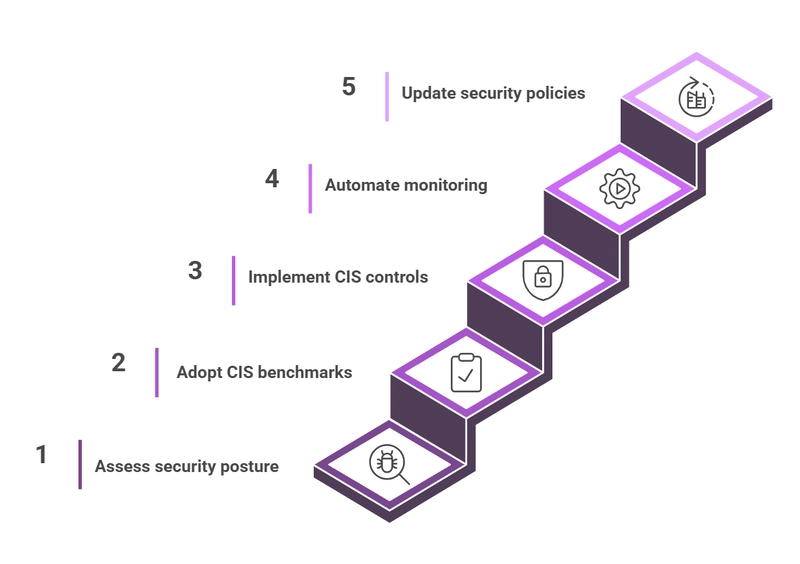
Complying with CIS standards requires organizations to implement a systematic approach to security. Here are the key steps:
- Assess your current security posture: Conduct a security audit to identify vulnerabilities in your IT infrastructure.
- Adopt CIS benchmarks: Configure systems according to CIS-recommended security settings.
- Implement CIS controls: Apply security controls such as asset management, continuous monitoring, and data protection measures.
- Automate compliance monitoring: Use automated tools to track configurations and detect deviations from CIS standards.
- Regularly review and update security policies: Keep security settings updated to address emerging threats and new CIS recommendations.
The challenge of staying CIS compliant
Achieving and maintaining CIS compliance isn’t easy. IT teams often struggle with manual audits, misconfigurations, and inconsistent enforcement across distributed environments.
One way to streamline compliance efforts is by using a CIS checklist—a structured set of security guidelines that helps organizations verify adherence to CIS benchmarks. Acting as a step-by-step reference, this checklist ensures IT environments remain secure by enforcing essential security practices, such as:
- Implementing strong authentication policies – Ensures only authorized users can access critical systems
- Disabling unnecessary services and ports – Limits exposure to cyber threats by closing unused entry points.
- Configuring firewalls and network security controls – Blocks malicious traffic and enforces secure communication.
- Monitoring system logs for suspicious activity – Identifies anomalies early to prevent security breaches.
- Regularly updating and patching software – Fixes vulnerabilities and safeguards against exploits.
While a CIS checklist provides a solid foundation for compliance, manually enforcing these security measures can be time-consuming, error-prone, and difficult to scale. Without automation, compliance efforts become a constant uphill battle.
How ManageEngine Network Configuration Manager simplifies CIS compliance
Organizations need a solution that automates compliance enforcement and eliminates configuration drift. That’s where ManageEngine Network Configuration Manager (NCM) plays a crucial role:
- Automated compliance audits: Detect non-compliant configurations instantly.
- Predefined CIS Policies: Enforce security settings without manual intervention.
- Real-time alerts: Get notified of unauthorized changes before they lead to breaches using real-time change notifications
- Automated compliance enforcement: Automate the process of fixing misconfigurations and enforcing compliance across your network remotely using Configlets.
- Detailed compliance reports: Generate audit-ready compliance reports to demonstrate adherence.
With cyber threats evolving rapidly, manual processes are no longer enough. A proactive compliance strategy powered by automation ensures your network remains secure, resilient, and always CIS-compliant.
Strengthen your organization’s security posture with ManageEngine Network Configuration Manager—because compliance isn’t just about rules, it’s about resilience. Download a free 30-day trial to get started today!
Authored by – Akash Arun Babu